TrustSource @ LSEC on SBOMs
Let’s meet at the IIOT SBOM Nov. 10th!
Thank you @ LSEC – Leaders In Security for inviting us to talk about #SBOM #DevSecOps and the upcoming challenges form the security point of view. @Jan will address the challenges around generating SBOMs, how to tackle it on the automation side in his talk “Getting the SBOM right, and then?”. Further on the talk will address thoughts on the life cycle perspective, what comes after the SBOMs creation. It also will also report about the work the #LinuxFoundation #OpenChain Automation work group is performing as well as invite to a new sort of SBOM user group, outlining best practises on defining SBOMs.
Looking forward having great conversations and learn even more about the challenges you are facing while creating SBOMs in the IIOT world.
C U there!
Gleaning
(22.11.22) Thank you very much for the kind hosting and the gerat exchange to all other speakers and participants at the IIOT SBOM. It has been great to learn about your demands and thoughts. Looking forward talking to you further. All speeches have been recorded and are avialble at the IIOT SBOM website. Jan’s talk we linked here.
It is split into two sections due to coordination with some speakers from different time zones. However, the first part addresses the SBOM and its contents. What should go in, what is a suitable format and what are the benefits of producing SBOMs (besides compliance with regulatory requirements). The second part addresses SBOM creation automation, transfer a few experiences from the legal SBOM design and spins a few thoughts on what you may do with SBOMs whilst they are around.
Free Open Source Compliance Training
For years, the same questions have arisen again and again in the context of open source:
- Am I allowed to use open source in applications used for business purposes?
- What are the consequences of using open source?
- Is the GPL a “toxic” license?
- What do the American licenses mean for us in Europe?
The irritation hits developers in particular, who are confronted with the use or deployment of open source in the front line. Now, computer scientists are rarely also lawyers, and even if law and computer science are similar in many aspects, it is not trivial to interpret a license without prior legal knowledge.
To help overcome this gap, we have provided a basic Open Source Compliance – Training. The training introduces the topic, briefly describes the background and gives insight into the essential aspects of licenses. More than 4 hours of video material, presentations and quizzes have been incorporated into the freely available, self-paced online training course.
The presentations, held in English, are divided into small, short bites, so that they can be easily consumed in between online meetings or in short doses at the beginning of each day.
Direct access can be found here on the Trainings page.
ISO 5230 - Standard on open source compliance
December 14th, 2020, the International Standardisation Organization (ISO) publicly released ISO 5230, the first standard on open source compliance (OSC). The standard is a result of several years work of a working group under the umbrella of the linux foundation. Since several years many cope source compliance experts from leading technology organisation worldwide sat together and shaped a simple, but efficient approach on how to tackle the open source compliance challenge.
The following video – a recording of the 10 min introduction to the OpenChain project Jan held Feb 6th @ this years FOSDEM – explains the core idea of the OpenChain project and introduces the core specification requirements (outline of the ISO 5230).

You think that ISO 5230 is relevant for your company? You want to learn more?
Do not hesitate to reach out for a quick chat!
OpenChain helps to build trust along the value chain by requiring certified participants to comply with specified requirements on how to arrange their open source usage and management. Since we are involved with OpenChain for several years now, we took the ideas and embedded them into TrustSource. Thus TrustSource is best suited to support the introduction as well as the ongoing compliance with ISO 5230, respectively the OpenChain requirements.
Interested to get a better understanding of how TrustSource may support your OpenChain/ISO5230 certification?
New release v1.7 introduces Notice-file-Generator
We are proud to announce the long awaited Notice File Generator. With this tool the time consuming digging through files and collection of license information belongs to the past. With the Notice-File Generator it will be available in only one click!
For all scanned projects TrustSource evaluates resulting obligations depending on project context. For each license-component combination the resulting documentation requirements are derived and the information will be assembled into the Notice-File. Wherever change notices or author credits will be required, TrustSource will try to fill the information from its Knowledgebase or outline a Todo. So the Compliance Managers work can focus on closing the gaps. Due to our shared open source component base, digging for authorship or copyright information must not be done, where another customer already did the job. This will reduce clearing time a lot!
In addition to that we renovated and extended some of our plugins. Now it is possible to break your build based on the results of a scan, e.g. on violations using most of the plugins. This extends your compliance control over the CI/CD chains. Also proxy capability has been added, so that a use behind corporate firewalls is possible as well.
The new user management allows free accounts to login using Github or LinkedIn-accounts. Also the new Identity Management introduces the option, to add multiple roles to a single user inside the same company. This increases the flexibility of your role design. Starting from corporate versions on, also Multi-factor-authentication is available. Integration of LDAP and other identity providers is available as well.
Read more about the features in our Knowledge base.
New Release v1.6 available
We are happy to announce availability of v1.6! Also v1.6 comes with massive new features, focused on process improvements. Read more:
New Features
- Vulnerability-alert - It took us quiet a bit, to get the matching towards a reasonable quality, but we manged it after all. You will now get notified by TrustSource, if new vulnerabilities appear for components that you are using in your most recent build.
- "Action required" items in inbox - Especially for our compliance managers we provide an in box on the dashboard listing all open approval requests. This allows you to immediately see, where action is required.
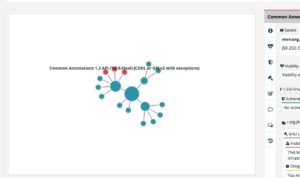
- Dependency graph - The so called dependency list is a flat list of all components entering the project even through transitive dependencies. To allow a better understanding of the impact this component has, the graphical display allows to actually _see_ the position within the dependency graph. You may modify the appearance and expand or shrink single nodes for better visibility.
Improvements
- Improve rule sets - Based on customer feedback and own research, we were able to improve the analysis results of several licenses.
- Improved maven Plugin - The maven plugin has been extended to support the check functionality allowing to verify components on dev-desktop without the need to push a scan.
- Improved Jenkins Plugin - Also the Jenkins plugin has been extended to use the transient version of the check-API.
Fixes
- Add name in register form - Changing your name after having been invited while login in the first time is possible now.
- Propagate deletion of all members - Changing members of a project respectively a all modules within a project at once has been introduced since a while. But it has not been recognized that the propagation of an empty list does not immediately take effect. This has been fixed now.
Our next version v1.7 will focus on security and extend the login capabilities. We will introduce alternative ways to authenticate and simplify corporate SSO. The given role model has been reviewed and will be tuned towards more flexibility.
If you want to get an overview or some insights in to our roadmap, feel free contacting our sales team! They will be happy presenting you the upcoming steps.
If you feel like there should be some features you do not see on the horizon, please let us know! Our business development or your engagement manager will be happy to hear about your ambitions.