TrustSource @ FOSDEM 2021
TrustSource @ FOSDEM 2021
we are looking forward to the presentations of @Jan Thielscher & @Grigory Markin at FOSDEM 2021.
Open Source Compliance Tooling – Capability Reference Architecture
Jan will present the Open Source Tooling Workgroup‘s reference model in the OpenChain Dev-Room , which outlines domain-specific capabilities and their interrelationships. The model has been created over the last two years by members of the workgroup and is intended to provide an overview of the required tasks that will be needed in the context of open source compliance. It is also useful for mapping the different tools or being clear about what functionality they cover. See the complete video here.
During the talk Jan will also try to motivate tool vendors to map their tools against the model.
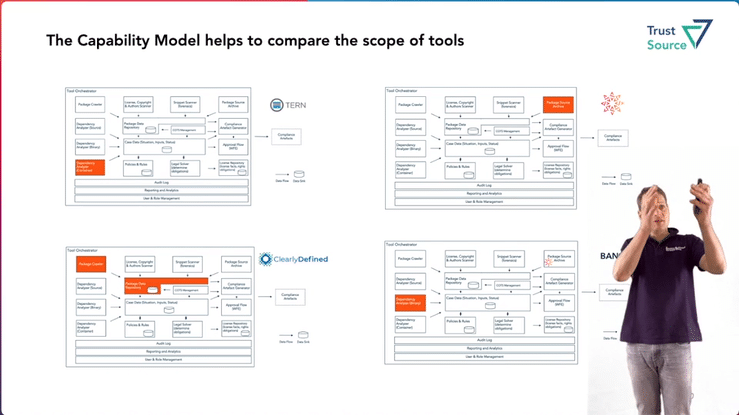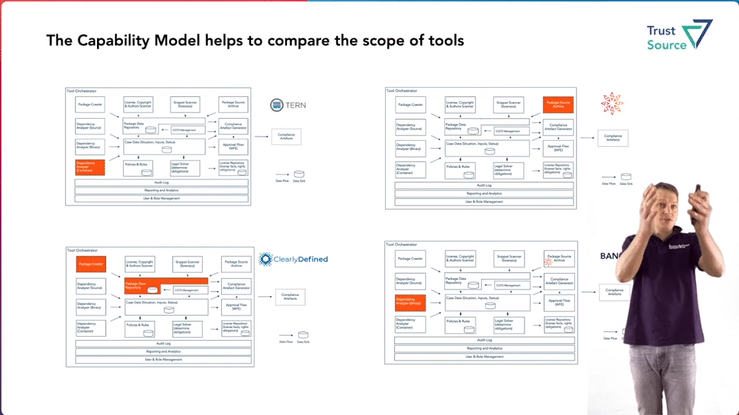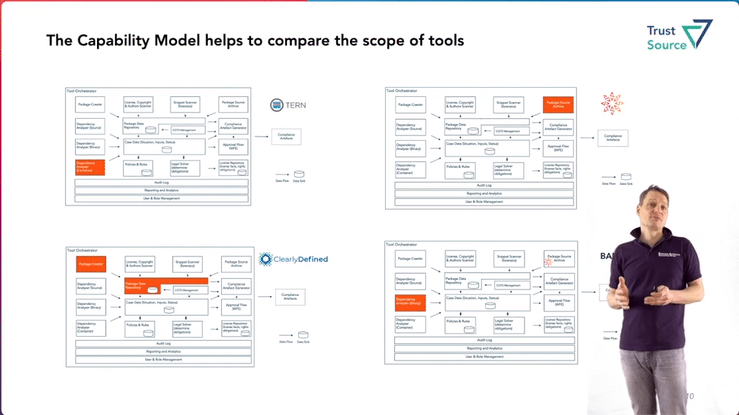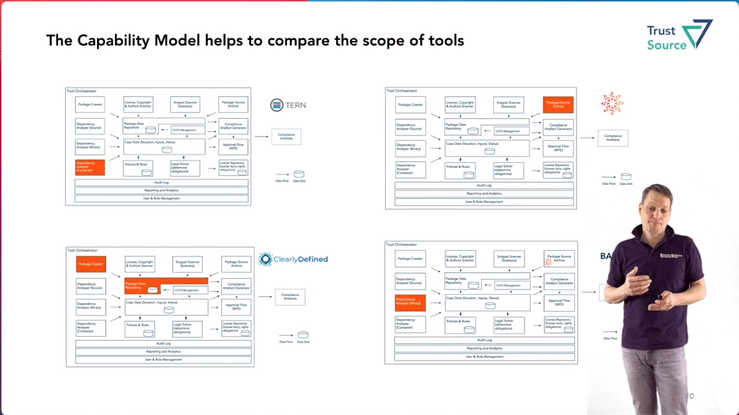
In a second talk, Grigory Markin will present the TrustSource DeepScan open source tool and the free online service DeepScan of the same name in the Dev-Room Software Composition. This solution has been developed to support open source users in identifying the effective licenses and attribution information (license & copyright) :
TrustSource DeepScan – How to effectively excavate effective licenses
In this 15 minute talk, Grigory and Jan will briefly outline the challenge of “effective” licenses and discuss the various technical possibilities and challenges of automated license analysis using similarity analysis, among other things. Finally, the tool, the current state of work and the next steps will be briefly presented.
ISO 5230 - Standard on open source compliance
December 14th, 2020, the International Standardisation Organization (ISO) publicly released ISO 5230, the first standard on open source compliance (OSC). The standard is a result of several years work of a working group under the umbrella of the linux foundation. Since several years many cope source compliance experts from leading technology organisation worldwide sat together and shaped a simple, but efficient approach on how to tackle the open source compliance challenge.
The following video – a recording of the 10 min introduction to the OpenChain project Jan held Feb 6th @ this years FOSDEM – explains the core idea of the OpenChain project and introduces the core specification requirements (outline of the ISO 5230).

You think that ISO 5230 is relevant for your company? You want to learn more?
Do not hesitate to reach out for a quick chat!
OpenChain helps to build trust along the value chain by requiring certified participants to comply with specified requirements on how to arrange their open source usage and management. Since we are involved with OpenChain for several years now, we took the ideas and embedded them into TrustSource. Thus TrustSource is best suited to support the introduction as well as the ongoing compliance with ISO 5230, respectively the OpenChain requirements.
Interested to get a better understanding of how TrustSource may support your OpenChain/ISO5230 certification?
TrustSource DeepScan - Catch effective open source licenses
TrustSource DeepScan - CLI, web-based or as part of service
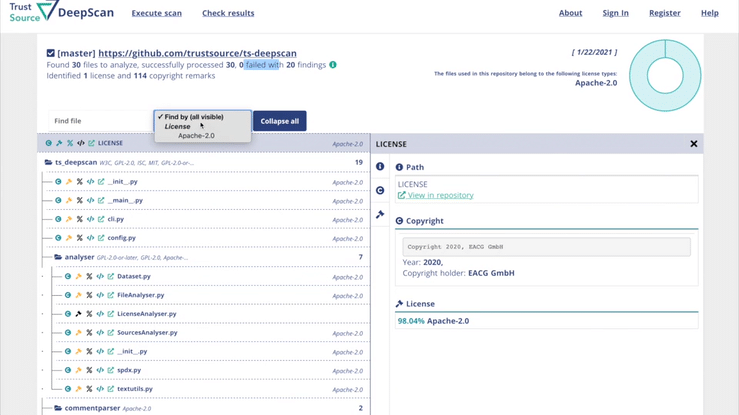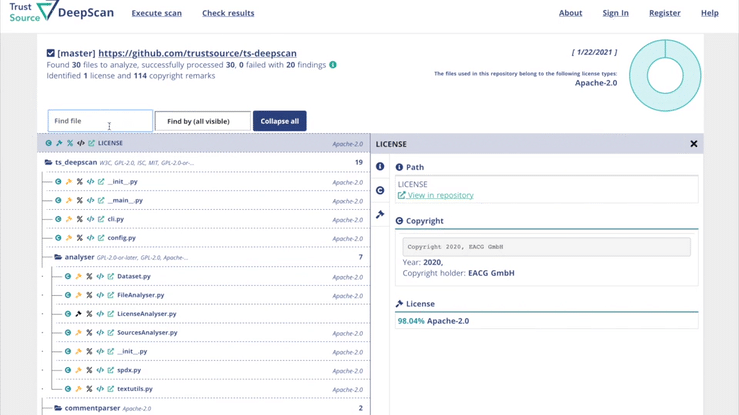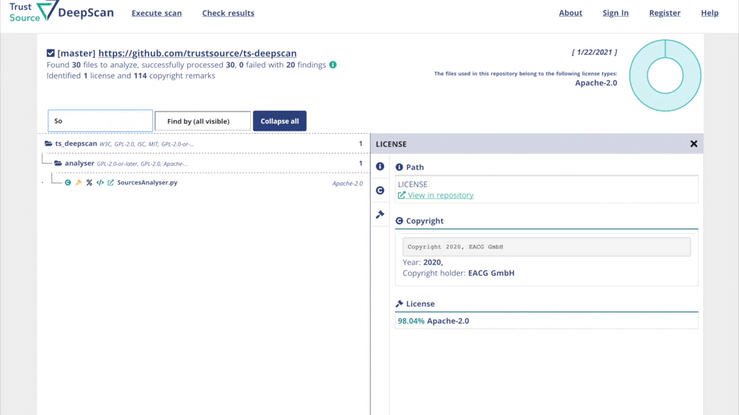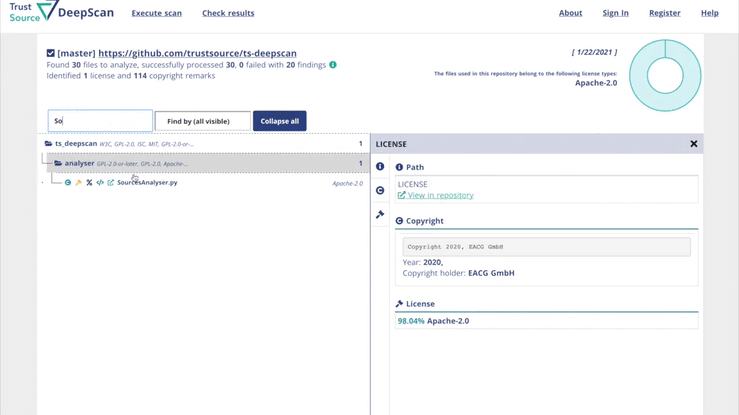
DeepScan is an open source tool, helping you to achieve open source compliance. You may use DeepScan to scan the repositories of your solution or the components you are applying. It will identify all license and – if wanted – copyright information. This is relevant to ensure that you have the correct understanding of the rights and obligations associated with the open source components you are using.
DeepScan is available in three flavours:
While the CLI version is fully functional, it requires the user to assess the results file by himself. The CLI-version can publish its findings either in standard out or in a file using JSON. The web-based UI provides a comfortable way to watch and work with the results. The solution integrated with TrustSource allows you to amend the findings and share your data with others.
Why are effective licenses so relevant?
Everybody developing software should have an understanding about the components he is using to provide his solution due to two reasons:
- Legal compliance
- Security
Getting a grip on legal compliance
From the legal perspective, it is essential to understand what your solution consists of. Open source does not imply free goods. Just to have free access does not mean you are free from obligations. Often open source components come with a license that requires the user to comply with certain obligations. In many cases the right to use is bound to the compliance with some obligations, e.g. attributing the copyright holder.
Theoretically every component can have its own license. In practice it turns out that there are roundabout 400 licenses and a countless number of derivates that govern the usage of open source. Some are more, some are less restrictive. However, given you do not take care for the rights and obligations associated with the components you are using, you swiftly slide out of legal conformance. In the worst case official law enforcement might charge senior management of companies not effectively preventing such risk with professional fraud.
DeepScan helps to assess repositories for license indications, exposing all findings in a comfortable way. Compiled into one reult, with links into the depth of the repository allowing fast tracking and review.
Give it a try!
No installation or registration required…
Keeping track of what is used improves security
The second reason, why you better should be aware of the components inside your solution is, to learn early about issues associated with such components. Given you have the structures of your solutions scanned with TrustSource, all versions of the builds are chronologically available. trustSource checks NVD and other vulnerability boards for updates and compares incoming data with its components information. If you use – or have used – a vulnerable component, you will get a notification.
This gives you an advantage over potential malicious actors. You may inform your customers still using vulnerable versions, start working on fixes or at least help them to prevent misuse by malicious actors.
So you see, there are many reasons, why you should know what is inside your code base….
To learn more about the different DeepScan solutions we provide, see this short video introduction. This speech will be provided at FOSDEM 21 in the Software Composition Analysis DevRoom.
Visual Studio plugin extension for .Net-framework available

Today we are proud to announce the availability of the new Visual Studio plugin, allowing to scan .Net-Core and .Net-Framework projects in parallel with one plugin only. The simplest way to obtain the plugin will be through the Visual Studio marketplace. As the plugin itself is open source, you will find the code also on github.
Continuing our initiative to bring TrustSource – the modern art of open source management – to the Microsoft developers community, we have combined both worlds in one plugin. Thus allowing you to operate both implementations in one solution.
Out next step on the road will be to extend the commandline-capability for the combined solution, allowing you to integrate the scanning also with your CI/CD chain. We expect this to be available by the end of March.
Feel free contacting us any time, to clarify questions, feedback usage experiences or issues you experience throughout the installation. We are happy to hear from you!
New release v1.7 introduces Notice-file-Generator
We are proud to announce the long awaited Notice File Generator. With this tool the time consuming digging through files and collection of license information belongs to the past. With the Notice-File Generator it will be available in only one click!
For all scanned projects TrustSource evaluates resulting obligations depending on project context. For each license-component combination the resulting documentation requirements are derived and the information will be assembled into the Notice-File. Wherever change notices or author credits will be required, TrustSource will try to fill the information from its Knowledgebase or outline a Todo. So the Compliance Managers work can focus on closing the gaps. Due to our shared open source component base, digging for authorship or copyright information must not be done, where another customer already did the job. This will reduce clearing time a lot!
In addition to that we renovated and extended some of our plugins. Now it is possible to break your build based on the results of a scan, e.g. on violations using most of the plugins. This extends your compliance control over the CI/CD chains. Also proxy capability has been added, so that a use behind corporate firewalls is possible as well.
The new user management allows free accounts to login using Github or LinkedIn-accounts. Also the new Identity Management introduces the option, to add multiple roles to a single user inside the same company. This increases the flexibility of your role design. Starting from corporate versions on, also Multi-factor-authentication is available. Integration of LDAP and other identity providers is available as well.
Read more about the features in our Knowledge base.
.Net-Core Support available

We are proud to announce new tools to support scanning of .Net-Core projects today. You will find the platform independent tool in our public repository on Github.
The tool allows to scan .Net-core projects and transfers the list of dependencies to our platform for further analysis. There the identified components will be reseached for license and vulnerability information and legal obligations depending on the usage context will be derived.
It consists of two parts: The first part is the Scanner itself. This part is taking care for the dependency resolution and assembly of all relevant data. The second part is the Console App, which is developed to allow command line interaction with the scanner.If executed from within the project path, an execution might be triggered with a statement as simple as
$ dotnet TS-NetCore-Scanner.dll -user “user@domain.com” -key “TrustSource Key”
While the console application itself is written in .Net-Core and thus more or less platform independent, the corresponding Visual Studio plugin is available for the Windows platform only. If you feel like the Visual Studio Plugin for .Net-Core should be available on other platforms as well, please let us know!
Finally we close this relevant gap in our tooling landscape. Together with the new Nuget-crawler we have provided, the .Net-Core-Developer now can experience the same level of quality, like other Developers already do quiet a while. But this is not enough. There is more to come:
In a next step we will extend the plugin with the capability to also scan .Net-Framework projects as well. This will bind the solution to the windows platform, which is where we see most of the Visual Studio developers delivering.
We hope those of you enjoying the Microsoft development world now will start enjoying TrustSource as well. Please feel free to reach out in case of questions or ideas on how we may improve the plugins! We are happy to learn about your usage experiences.
New Release v1.6 available
We are happy to announce availability of v1.6! Also v1.6 comes with massive new features, focused on process improvements. Read more:
New Features
- Vulnerability-alert - It took us quiet a bit, to get the matching towards a reasonable quality, but we manged it after all. You will now get notified by TrustSource, if new vulnerabilities appear for components that you are using in your most recent build.
- "Action required" items in inbox - Especially for our compliance managers we provide an in box on the dashboard listing all open approval requests. This allows you to immediately see, where action is required.
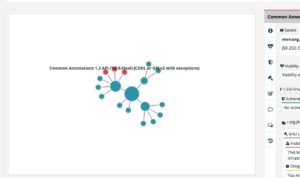
- Dependency graph - The so called dependency list is a flat list of all components entering the project even through transitive dependencies. To allow a better understanding of the impact this component has, the graphical display allows to actually _see_ the position within the dependency graph. You may modify the appearance and expand or shrink single nodes for better visibility.
Improvements
- Improve rule sets - Based on customer feedback and own research, we were able to improve the analysis results of several licenses.
- Improved maven Plugin - The maven plugin has been extended to support the check functionality allowing to verify components on dev-desktop without the need to push a scan.
- Improved Jenkins Plugin - Also the Jenkins plugin has been extended to use the transient version of the check-API.
Fixes
- Add name in register form - Changing your name after having been invited while login in the first time is possible now.
- Propagate deletion of all members - Changing members of a project respectively a all modules within a project at once has been introduced since a while. But it has not been recognized that the propagation of an empty list does not immediately take effect. This has been fixed now.
Our next version v1.7 will focus on security and extend the login capabilities. We will introduce alternative ways to authenticate and simplify corporate SSO. The given role model has been reviewed and will be tuned towards more flexibility.
If you want to get an overview or some insights in to our roadmap, feel free contacting our sales team! They will be happy presenting you the upcoming steps.
If you feel like there should be some features you do not see on the horizon, please let us know! Our business development or your engagement manager will be happy to hear about your ambitions.
Understanding the most important vulnerability acronyms
Since the Equifax event, vulnerability management gained a lot of attention. But what does "vulnerability" or "known vulnerability" mean? How to handle such an information? And why is this particular important to open source components?
To answer all these questions, we will publish a short series of articles. First we will dive into the goals of vulnerability management and basic concepts. Then we point our attention to the process of vulnerability management and finally show, how TrustSource may support you in performing these tasks.

The goal of vulnerability management
The goal of vulnerability management should be to MINIMIZE THE POSSIBLE ATTACK SURFACE of your environment, where "the environment" may be any scope of software you define (a SaaS, a software package or a complete enterprise). Minimizing the attack surface on the one hand means to accept that there will remain a risk. On the other hand, it means to know all possible attack vectors, assess the risk (maximal loss) associated and derive measures well suited to reduce the attack surface to a financially acceptable risk. This said, it is absolutely essential to assess your environment applying the most recent knowledge - known vulnerabilities - and to address all critical aspects.
The acronyms and concepts
This goal sounds ambitious. But no panic! tehre are some concepts out there helping you to do the job. Before we step into the process, we advise to familiarize with the following few abbreviations , terms and concepts:
-
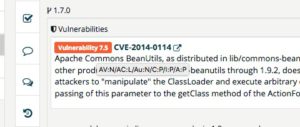
CVSS = Common Vulnerability Scoring System
has been introduced to measure the impact of a vulnerability. Has a scale of 0-10, with 10 the highest, most critical. Everything above 7.5 may be considered as critical. CVSS is currently in v3, however, vulnerabilities reported prior to 2016 will have been reported in CVSS v2.
-
CAV = Common Attack Vector
describes the identified attack covering aspects such as prerequisites to execute the attack, impact and effect the attack will have. in v3 this will be attach vector (AV), attack complexity (AC), priviledges required (PR) and UI (User interaction). In version 2 (pictured in the tool tip on the right) you will see attack vector (AV), access complexity (AC), Authentication (Au), as well as the impacts on Confidentiality (C), Integrity(I) and Availability (A).
The standardized description of the attack vector is a great help when it comes to understand the impact a potential threat or a vulnerability may have.
-
CVE = Common Vulnerability and Exposure
The CVE is a key identifying a particular vulnerability. The key consists of the three letters CVE, the year and a counter. The counter is assigned by an assigning authority. The counter has no other meaning than to differentiate the particular vulnerability and exposure entries. It gets assigned in the moment it is requested. To request a number, no evidence is required. However, between assignment of an ID and its confirmation several weeks or months may pass.
-
CPE = Common Platform Enumeration
To provide a sound capability to match a vulnerability with the components concerned, the CPE has been introduced. Each component that has a vulnerability assigned, receives a CPE - currently following specification v2.3. A CPE is a unique identifier of a product allowing to refer back from the vulnerability to the product. The CPE (v2.3) consists of a type (h=hardware, o = Operating system, a = application), vendor, product and version information. A central directory, the CPE-dictionary contains all CPEs ever assigned.
However, the matching of CVEs with its assigned CPEs to real life components is critical. Wrong matches lead to false positives, putting the cat under the pigeons; missing matches leave vulnerabilities untreated. That is why we do spend so much attention on accuracy here.
-
CWE = Common Weakness Enumeration
This is a list of weaknesses found in applications. It is a community approach led by MITRE and SANS Institute, supported by huge number of technology heavy weights listing all kind of weaknesses, outlining their inner workings, exploit code and more details. CVEs may have a link to the corresponding weaknesses. the list is a great resource for security experts as well as wanna-be-hackers. It helps to understand the way attacks are created as well as what causes attacks to be successful.
The information supports the understanding of the impact a vulnerability really may have on the individual application.
So what?
Having read all this, you may want to turn your back at the topic and say, "Well, sounds good. Seems like all settled. Why bother?". Yes, there is a lot of structural work that has been done. But it these structures have only been created to allow you doing the job efficiently. The job still needs to be done. In our next post on vulnerabilities, we will cover the process on how to really assess a vulnerability and derive useful action.
EACG and OpenChain agree on partnership
Frankfurt, June, 8th 2018, EACG - the mother company of TrustSource - and the Linux Foundation agree on a partnership to co-operate in the OpenChain project.
EACG acts for several years now in the field of open source governance and compliance. Based on the experiences from some larger projects, EACG has developed TrustSource , the platform for automation of open source governance. "We are close to having all of the stuff automated. Even the legal part!", summaritzes Jan the efforts over the last few years.
"Our platform delivers the technical part: scanning, mapping, documentation and reports. But Governance is much more, that a tool may do. To really ensure compliant software delivery and distribution also processes and culture need to change. This is where OpenChain comes in. The many, well thought and carefully designed requirements will lead towards the required change, if managed carefully. We support that and provide all required features to ensure OpenChain compliance. "
EACG offer consulting services in the area of open source compliance and governance as well as the solution platform TrustSource. there are different editions available according to your needs. To check it out and test it here.
Release v1.5 available
We are happy to announce our latest Update v1.5.16. With this release we further strengthen our capabilities in managing vulnerabilities and extend our documentation competencies.
New Features
- PDF-your-Reports - It is now possible to download your reports as PDF. Timestamp and release number will always be included, so there is not chance for mixing up data.
- New Bill of Materials Report - With this release we have provided a BoM-report allowing you to request a visual representation of the Bill of Materials of any of your projects.
- New CVE-Impact Report - With this report you may select a CVE number and immediately see which components in what project are affected by this CVE. From the report you may jump directly to corresponding components and trigger further action.
Improvements
- Branding changed to TrustSource - from now on we have moved to the new branding schema. Not only the visuals (logo, etc.) changed, but also the URLs. The base URL is no longer https://ecs-app.eacg.de but it is https://app.trustsource.io. The old URLs will remain working, but we suggest to use the new ones.
- Preview changes in Bulk user upload - The bulk user upload for the corporate and enterprise accounts does have a preview now. So you may see which lines might cause unwanted impacts and dry-run your import before allowing it to take effect.
- Jira-Status-Report - Jira tickets are now presented in a nicer way according to status. Also it is possible to have project specific reports.