Based on the events surrounding the Shai-Hulud worm, we have adjusted the basic configuration of our SCA scanner ts-scan. In its standard configuration, it no longer executes scripts from the <scripts> section of package.json. Instead, a warning is issued that there may be an insecure configuration. To execute the scripts anyway, the parameter node:enableLifecycleScripts must be explicitly added to the scan call from version 1.5.2 onwards.
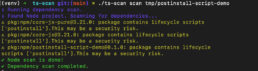
We recommend that our customers and users update ts-scan to the latest version – v1.5.2 in this case – to better protect their environment from malicious activity triggered by unwanted script execution.
PLEASE NOTE: This is not a vulnerability caused by ts-scan. The ability to embed arbitrary scripts in package.json and have them executed is a feature of the Node environment. This has existed for quite some time and was already discussed years ago as a potential security vulnerability. However, no action has been taken against it so far.
