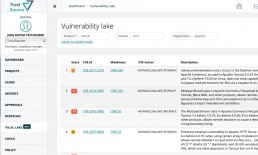
Vulnerability Lake in beta
TrustSource adds Vulnerability Lake
Due to many requests we decided to open up our internal vulnerability DB for research by developers. Starting from version 2.0 TrustSource will provide its internal “known vulnerability” database for search. There will be several searches available:
- TrustSource Vulnerability-Lake public web UI
- TrustSource Vulnerability-Lake web UI
- TrustSource Vulnerability-Lake API
The public web UI as well as the TrustSource integrated web ui provide a simple and an expert search mode. You …
TrustSource Vulnerability Lake allows simple overview of vulnerability status
TrustSource DeepScan - Catch effective open source licenses
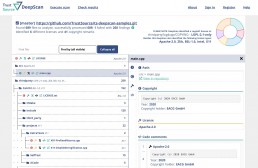
TrustSource DeepScan - CLI, web-based or as part of service
DeepScan is an open source tool, helping you to achieve open source compliance. You may use DeepScan to scan the repositories of your solution or the components you are applying. It will identify all license and – if wanted – copyright information. This is relevant to ensure that you have the correct understanding of the rights and obligations associated with the open source components you are using.
DeepScan is available in three flavours:
While the CLI version is fully functional, it requires the user to assess the results file by himself. The CLI-version can publish its findings either in standard out or in a file using JSON. The web-based UI provides a comfortable way to watch and work with the results. The solution integrated with TrustSource allows you to amend the findings and share your data with others.
Why are effective licenses so relevant?
Everybody developing software should have an understanding about the components he is using to provide his solution due to two reasons:
- Legal compliance
- Security
Getting a grip on legal compliance
From the legal perspective, it is essential to understand what your solution consists of. Open source does not imply free goods. Just to have free access does not mean you are free from obligations. Often open source components come with a license that requires the user to comply with certain obligations. In many cases the right to use is bound to the compliance with some obligations, e.g. attributing the copyright holder.
Theoretically every component can have its own license. In practice it turns out that there are roundabout 400 licenses and a countless number of derivates that govern the usage of open source. Some are more, some are less restrictive. However, given you do not take care for the rights and obligations associated with the components you are using, you swiftly slide out of legal conformance. In the worst case official law enforcement might charge senior management of companies not effectively preventing such risk with professional fraud.
DeepScan helps to assess repositories for license indications, exposing all findings in a comfortable way. Compiled into one reult, with links into the depth of the repository allowing fast tracking and review.
Give it a try!
No installation or registration required…
Keeping track of what is used improves security
The second reason, why you better should be aware of the components inside your solution is, to learn early about issues associated with such components. Given you have the structures of your solutions scanned with TrustSource, all versions of the builds are chronologically available. trustSource checks NVD and other vulnerability boards for updates and compares incoming data with its components information. If you use – or have used – a vulnerable component, you will get a notification.
This gives you an advantage over potential malicious actors. You may inform your customers still using vulnerable versions, start working on fixes or at least help them to prevent misuse by malicious actors.
So you see, there are many reasons, why you should know what is inside your code base….
To learn more about the different DeepScan solutions we provide, see this short video introduction. This speech will be provided at FOSDEM 21 in the Software Composition Analysis DevRoom.
Module 2 - Open Source Compliance and Security

Module 2 - Achieving Compliance and Security
- Goals:
Understanding of managing compliance and security risks, operational fulfilment using TustSource -
- Contents:
Compliance & Security goals, risk management approach, handling compliance risk, handling technical risk (security, viability),
Part I: achieving compliance , practical questions (cases), TrustSource tools to achieve compliance (understanding legal settings in detail, functionality of legal engine, private licenses, black- & whitelists for components and licenses, etc.), detailed assessment of a notice file, collecting attributions, change notifications making use of DeepScan to qualify sources, quizz
Part II: managing and assessing vulnerabilities, finding further vulnerability information, limitations of vulnerability data, examples analysing vulnerability data, using vulnerability reports, assessing viability, versions-analysis, forwarding tasks/tickets, handling developer versions, muting vulnerabilities, quizz
Part III: making use of infrastructure, 3rd party & COTS, handling private and commercial licenses, using linked modules in a different context , COTS report, SOUP list, quizz, Summary and test -
- Target Groups: project Managers, compliance Managers, developers
Module 1 - Compliance basics
Module 1 - Compliance Basics
- Goals:
Create awareness for the topic, introduce basic meanings -
- Contents:
Challenge of OSC (clarify direct vs. transitive dependencies) , recent and important cases, What if not?, basic terms, grants, obligations & their consequences, limitations and the termination of grants, matching to basic license classifications, check basic understanding, sample cases, roles and their responsibilities, general compliance process, Overview of the OpenChain specification, summary & test -
- Target Groups:
developers, administrators, compliance managers, product managers, project managers, senior managers
Module 4 - Developer Guidelines

Module 4 - Developer Guidelines
- Goals:
Provide understanding of relevant Compliance goals and artefacts , provide basic understanding of TrustSource elements as well as how to use them to achieve compliance -
- Contents:
Explain basic TrustSource constructs (Scans, Analysis, Reports, project settings, etc.), explain Compliance Artefacts (BoM, Notice File, SOUP-List, Compliance Report, etc.), clarify Developers responsibilities (Compliance & Security), TrustSource Support tools (using the UI, filtering, searching, dependency graphs), manage loose coupling and modification, how to manage settings, explain legal circumstances and their impact, Project manager responsibilities (Compliance & Security), TrustSource tools (Legal Analysis, Security Analysis, Viability Analysis, VersionCheck, different Reports), Understanding the approval flow, approval Dry-Run, integrating approvals (Git-flow, Github-flow), using projects and modules to structure work, running tests, using linked modules, adding infrastructure modules, integrating COTS, qualifying external repositories, sample assessments, resolution of sample cases (making it green), summary & test -
- Target Groups:
Developer, Project Manager, Administrators, Compliance Managers -
Module 5 - Procurement
Module 5 - Procurement
- Goals:
Understand the challenges to OS compliance poses to purchase departments - Contents:
Challenges in adding 3rd party and proprietary components, OS impact on purchasing agreements, managing 3rd party licenses in TrustSource, COTS & SOUP, components manager role, requesting 3rd parties to provide inbound BoMs, mutli-org-setup of TrustSource, alternative scanning approaches, summary & check -
- Target Groups: Purchasers, Developers, Project managers
Module 6 - Audit

Module 6 - Audit
- Goals:
Provide understanding of how to conduct an OS audit - Contents:
Scoping, the audit process, the deliverables, evidence, evidence, evidence, how to audit, escalation, version management, tooling support, binary analysis, source code analysis (repositories), build time analysis, legal compliance, security, other tests, what TrustSource can do for you, compiling a report, summary and check
- Target Groups:
Compliance Manager, Developer
Module 7 - TrustSource Administration

Module 7 - Tools & Tooling / TrustSource
- Goals: Provide basics of Tooling and TrustSource Administration
- Contents:
Open Source Compliance Capability map. matching open source tools, TrustSource Architecture, TrustSource Services, Users, LDAP & Identity integration, MFA, inviting external users, managing roles and rights, general settings, handling API and API keys, throtteling and usage limitations, configuring environment specific settings, using multi-entity setup, information about system status, contacting sup- port, stay tuned
- Target Groups: TrustSource administrators
Module 3 - Open Source Governance
Module 3 - Governance
Open Source Governance is key to achieve Open Source Compliance.
- Goals:
Understand the challenges of achieving and maintaining compliance across large organisations and how TrustSource may help - Contents:
understand the OpenChain Specification and OC Self certification procedu- re, Challenges of OS Compliance in large organisations, Goals of Governance, OS Governance Board and OS Governor, OS Policy ingredients, Policy distribution, TrustSource support for OS policy distribution, Inbound governance, Outbound Go- vernance, Committer Governance, Working contracts and OS Governance / work time vs sparetime, International law and work contracts in the context of OS gover- nance, managing OS and external workforces , Summary & test
Target group: compliance managers, CISOs, business unit respsonsibles
Module 8 - Recent Developments
Module 8 - Recent Developments
Open Source is on the move – tools, legal requirements and business models are constantly changing. This module gives an overview of the current developments of the last 12 months
- Current case law and new legal requirements
- New and updated licensing conditions
- Overview of new tools, features and functions
- Duration: approx. 60 minutes
Target group: developers, project managers, product owners, compliance managers, architects



