Quantum computing is just around the corner. Its capabilities will trash the security of many well known and widely used cryptography algorithms. Better prepare today for tomorrow’s changes. TrustSource allows you to find and catalogue algorithms in your codebase. Whether for Quantum Safety or export controls reasons, knowing what sort of encryption your solution is using will be important to maintain its security. Therefor we have enriched TrustSource with encryption management capabilities:
- Assess your or 3rd party code for encryption algorithms
- Catalogue the algorithms and their use
- Create CBOMs (Crypto bill of materials) and export them
- Assess your portfolio for the existence of particular algorithms
- Define policies to prevent use of broken algorithms
TrustSource does not only support to review your own code base, but to assess your 3rd party components as well.
Want to learn how to protect your apps from quantum impacts?
In this webinar you will learn about the state of quantum computing and what to expect when the systems will be available. Further on you will understand what you can do today, to prepare your apps to be safe when it becomes reality.
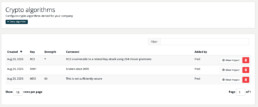
Identify cryptographic Algorithms
TrustSource tools can identify algorithms inside the code base. Whether you add them through source code or by adding cryptographic components. TrustSource SCA has various mechanisms to assess what you pull together for your software composition. And you may even add the SCANOSS as additional source of knowledge.
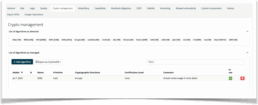
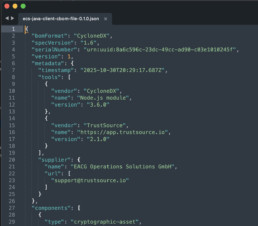
Export cryptographic asset information using CycloneDX
TrustSource has implemented the CycloneDX specification to export cryptographic asset information. This is an essential capability to share this essential information with stakeholders in the software supply chain or authorities.
With the “as managed” view, it is as simple as writing your groceries list to complete and export a CBOM. Give it a try!
Want to learn more Details on the Quantum Risk?
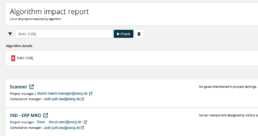
Assess your Portfolio for the Appearance of particular Algorithms
With TrustSource you will be able to assess your software portfolio for the appearance and use of specific algorithms. Whether you just want to know about the usage aof a particular algorithm or you want to understand the impact a recently broken algorithm has on your solution portfolio, TrustSource has the answer. Stop guessing, start knowing!
Define a Crypto Policy
To prevent the use of weak or already broken encryption algorithms you do not need any longer the expertise of crypto specialists. With TrustSource you may define the algorithms you do not want to be used in a deny-list (policy). Whenever one of these algorithms appears in any of your projects or components, this will be flagged – and in the most recent version – risks will be added accordingly. Thus, it will become transparent where encryption risks are hidden in your code base.